Dec 22, 2022
4 Authentication Schemes Every Developer Should Know

Authentication is the act of validating that users are whom they claim to be, and constitutes the first line of defense in any security process to prevent private data from falling into the wrong hands.
It can be single-factor, which means that only one verification will be made in order to assert a user’s identity, or multi-factor, which means that two or more verifications will be made.
In this article, we’ll cover 4 of most popular authentication schemes every developer should know.
Basic Access Authentication
Basic Access Authentication is an HTTP authentication scheme which consists in a client (e.g. web browser) providing a user name and password when making a request to a server.
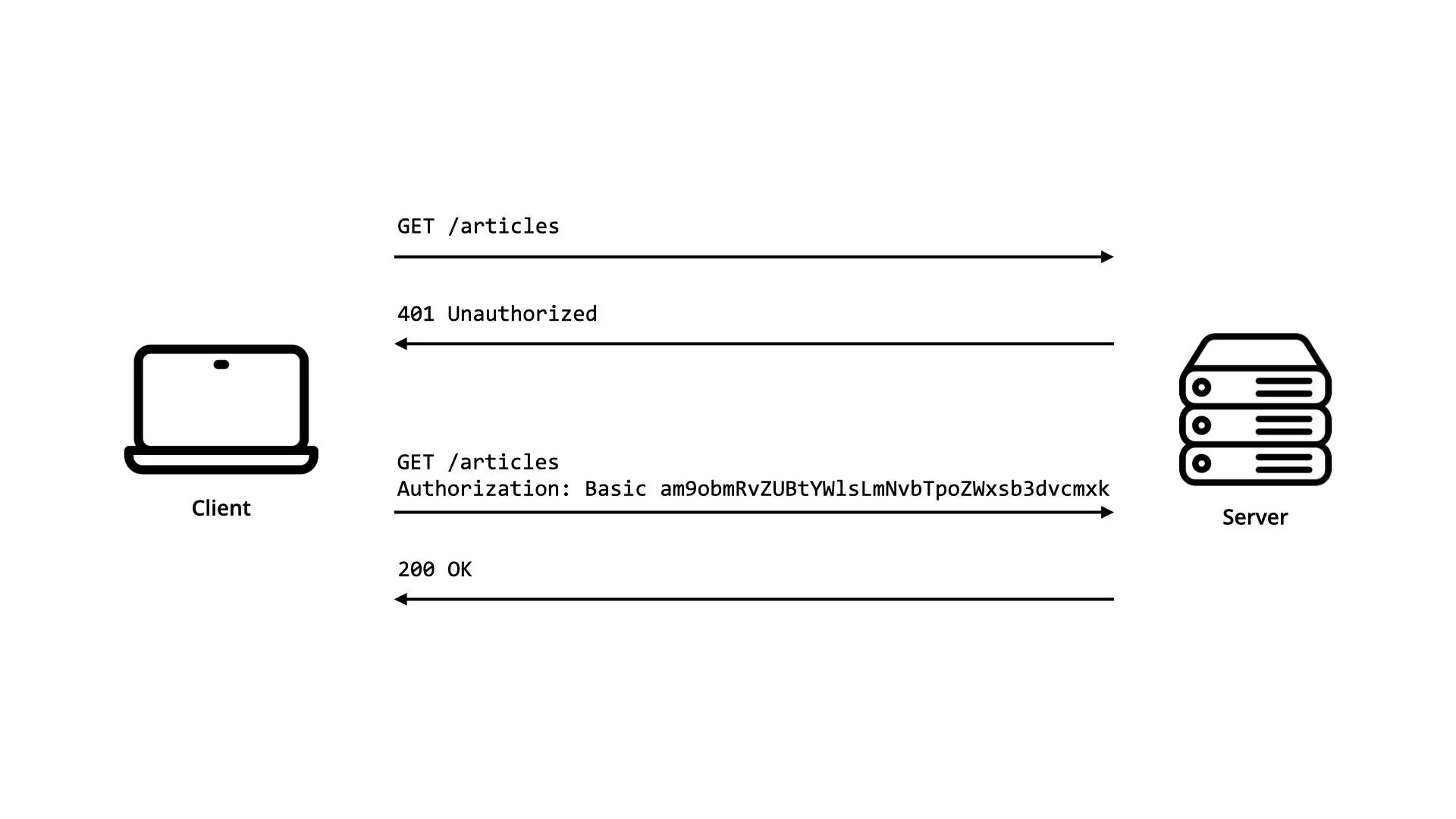
These credentials are specified in the Authorization header of the HTTP request in the form of a Base64 encoded string:
Authorization: Basic <credentials>
Where the user name and the password are concatenated with a single colon character (e.g. username:password).
As a reminder, encoding is the process of converting a piece of data into another form, in order to make it shorter or secret, but that can be easily reversed using the same algorithm — it’s main goal being to ensure data usability.
For example:
Authorization: Basic am9obmRvZUBtYWlsLmNvbTpoZWxsb3dvcmxk
Note that because the credentials are encoded and not encrypted, this method does not actually provide confidentiality protection, and must therefore be used in conjunction with HTTPS.
Bearer Authentication
Bearer Authentication is an HTTP authentication scheme that involves security tokens called bearer tokens.

Similar to Basic Access Authentication, it involves the use of a token placed in the Authorization header of the HTTP request. However, the difference is that this token is not client generated, but server generated in response to a login request.
Authorization: Bearer <token>
One thing to keep in mind though is that this type of token usually has a pre-defined validity duration measured in seconds, and will be considered expired by the system at some point.
When this happens, the client must request a new token from the server, which can be done either by inviting the user to go through the log in process again, or by using a more transparent mechanism called refresh tokens.
A refresh token is a special token that is sent alongside the access token, that has a greater validity duration, and that is used to transparently request new access tokens whenever they expire without the user noticing or having to perform any action.
A good practice though is to invalidate these refresh tokens once they’ve been used to request a new access token in order to protect the application from token compromise and replay attacks.
OAuth
OAuth which stands for Open Authorization is a protocol specifically designed to work with HTTP, that specifies a process for resource owners to allow a trusted authorization servers to issue access tokens for these resources to third-party clients.
A few years back, web and mobile applications started to heavily interact with each other, eventually enabling users to connect to a service using an account from another service — like for example using your Google account to log into your fitness or cooking app.
To avoid asking the user again for credentials, third-party applications used to keep the user’s password without encrypting it, which, aside from the security issue, implies that these applications were able to freely access any protected information.
To address these issues, OAuth 2.0 was created to allow interactions between applications in an optimal security context.
The OAuth protocol involves 4 actors:
- The resource owner.
- The client.
- The authorization server.
- The resource server.
Here’s a simplified overview of how the OAuth protocol works.
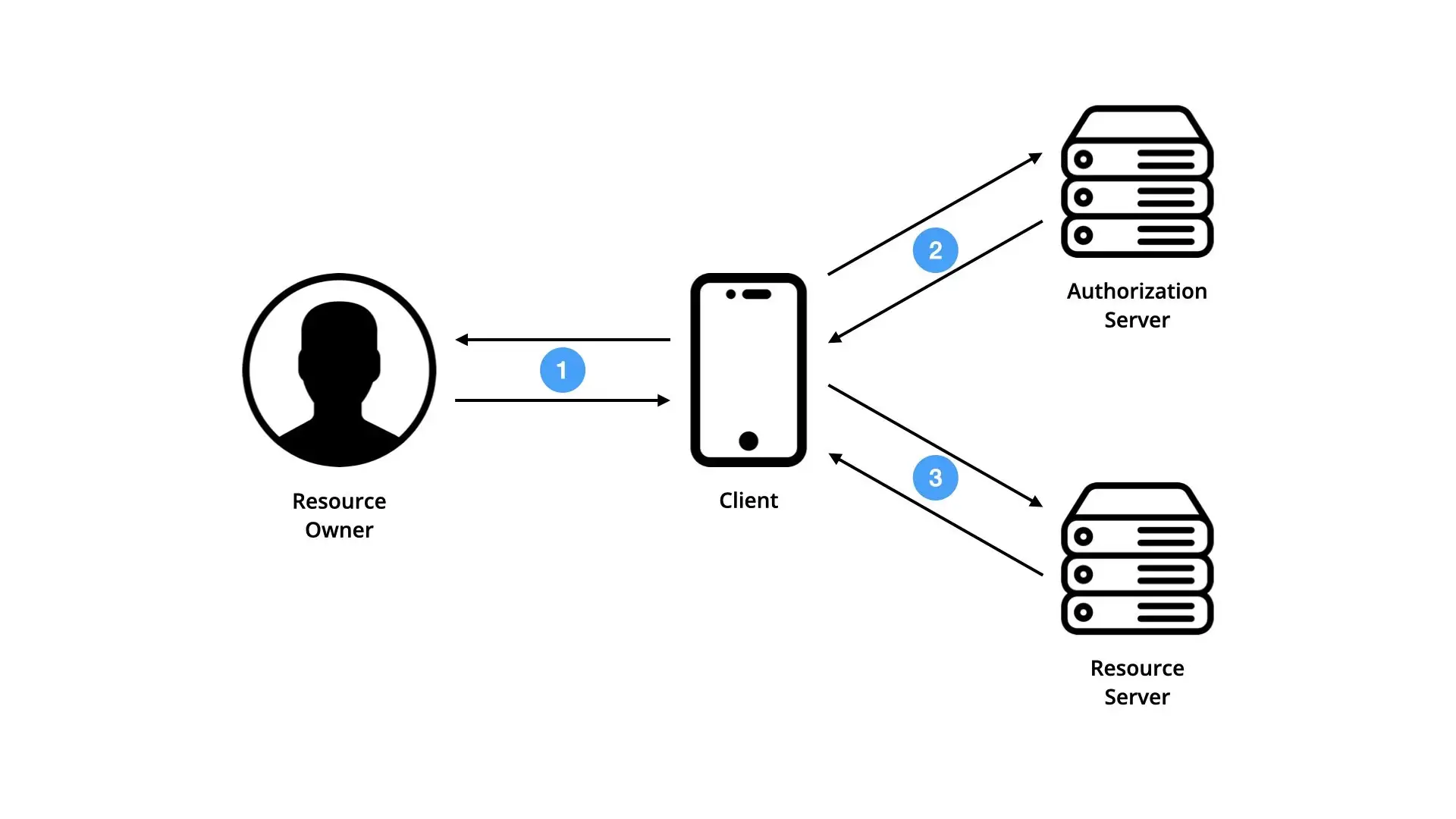
- The client (a third-party application or server) sends an access request to the resource owner (the user).
- The client then queries the authorization server, which in turn responds with an access token.
- Once the token acquired, the client is finally able to retrieve the protected resource by querying the resource server.
API Keys
An API key is a unique identifier — usually randomly generated — used to authenticate and grant certain access rights to a calling program to an API.
AidlASdkmudXbsdfgFLOmn4idsfsdhf
Unlike authorization tokens, API keys are specifically designed for projects and not users, as they are simply not as secure, since their value is easily retrievable within the source code that embeds them.
Beyond helping with identifying the project that makes the API call they’re also used to track and control how this interface is being used as:
- They help restricting IP ranges and operating environments.
- They enable the blocking of anonymous traffic that can be an indicator of potentially malicious activity.
- They help with API consumption by controlling and limiting the number of calls made to the API.
- They help to analyse and debug issues, one or more clients may experience.
It’s important to note that in contrast with tokens, API keys rarely expire but can easily be deactivated, simply by erasing them from the database.